In the present era of digital advancements, where technology has become an integral part of every facet of our lives, the significance of cybersecurity cannot be emphasized enough. While ethical hacking plays a vital role in securing computer systems and networks, there is also a darker side to hacking known as unethical hacking. This article delves into the concept of unethical hacking, its implications, and the measures taken to combat this cyber threat.
Definition of Hacking

Hacking refers to the act of gaining unauthorized access to computer systems or networks with the intention of exploring, manipulating, or stealing data. Hackers are individuals who possess advanced technical knowledge and skills to breach security measures.
Types of Hacking

Hacking can be classified into two main types: ethical hacking and unethical hacking. Ethical hacking, also known as penetration testing, is conducted by authorized professionals to identify vulnerabilities in systems and help organizations enhance their security. Unethical hacking, on the other hand, involves malicious activities and is performed without consent.
Ethical Hacking VS Unethical Hacking

The main distinction between ethical hacking and unethical hacking lies in their intentions and legality. Ethical hacking is conducted for the greater good, focusing on enhancing cybersecurity, whereas unethical hacking is motivated by personal gain or malicious purposes, and is deemed as illegal.
Unethical Hacking Explained
Definition of Unethical Hacking

Referred to as black hat hacking, is the practice of breaking into computer systems or networks without authorization for personal gain, damage, or disruption. Unethical hackers exploit vulnerabilities in security systems, steal sensitive information, and cause harm to individuals, organizations, and even governments.
Motivations of Unethical Hackers

Unethical hackers are motivated by various factors, including financial gain, revenge, curiosity, political activism, or simply the thrill of breaking into systems. They may target financial institutions, government agencies, healthcare organizations, or any entity that possesses valuable data or resources.
Cracking
Phishing is a technique used by unethical hackers to trick individuals into revealing sensitive information, such as passwords or credit card details, by impersonating a trustworthy entity. while attacks often occur through deceptive emails, messages, or websites designed to appear legitimate.
Malware Attacks

Unethical hackers employ various forms of malware, such as viruses, worms, Trojans, and spyware, to gain unauthorized access to systems, steal data, or disrupt operations. Malware can be distributed through malicious email attachments, infected websites, or compromised software.
Denial of Service (DoS) Attacks
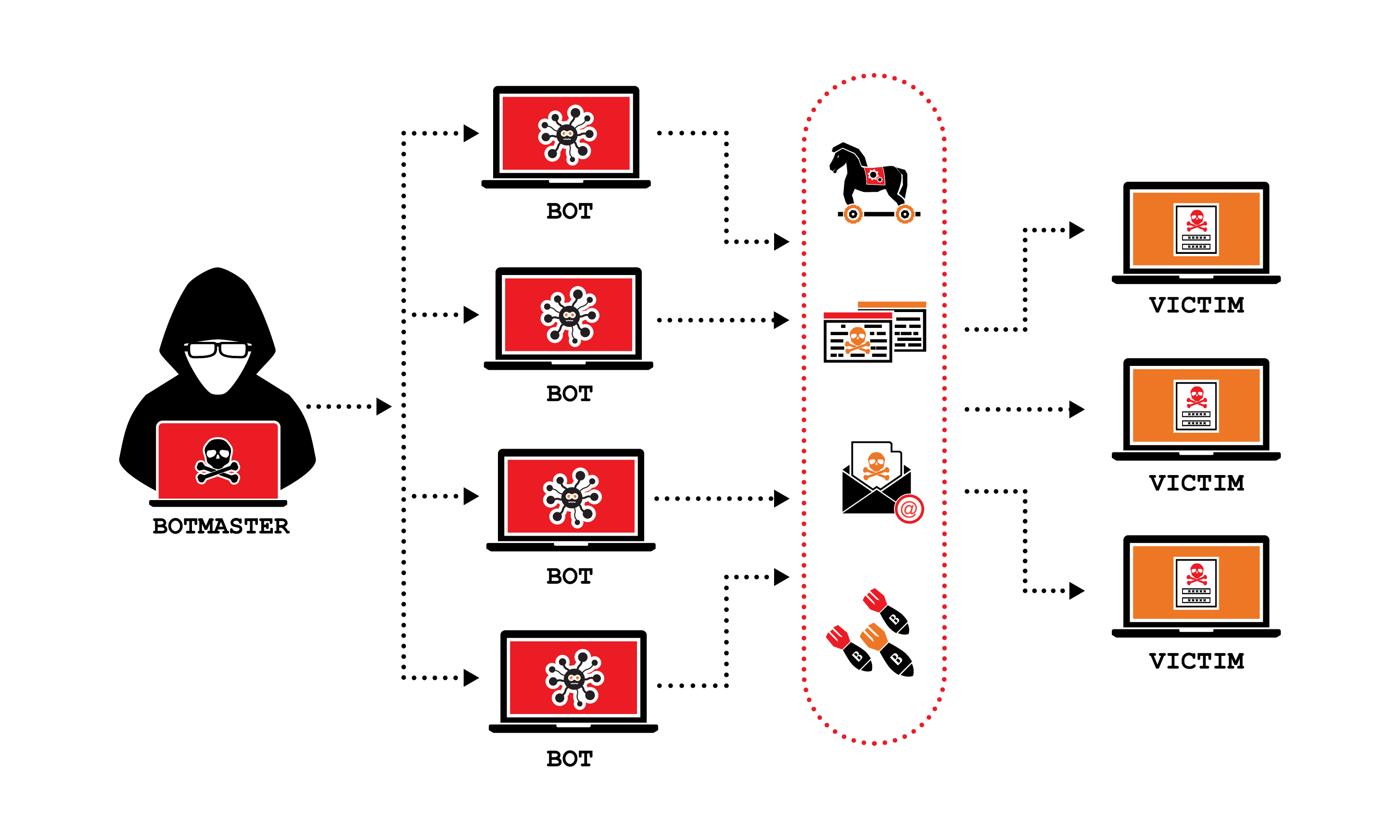
DoS attacks involve overwhelming a system or network with a flood of traffic, rendering it unable to respond to legitimate requests. Unethical hackers use botnets or other means to orchestrate massive traffic volume, causing disruption to services and making systems inaccessible to users.
Implications of Unethical Hacking
Financial Losses

Result in substantial financial losses for individuals and organizations. Cyberattacks can lead to the theft of intellectual property, financial data, or funds. The costs associated with mitigating the damages, recovering from an attack, and implementing enhanced security measures can be significant.
Breach of Privacy

Unethical hacking compromises the privacy of individuals and organizations. Personal and confidential information can be exposed, leading to identity theft, blackmail, or reputational damage. Privacy breaches can have severe emotional, financial, and legal consequences for the victims.
Damage to Reputation

When organizations fall victim to cyberattacks, their reputation and trustworthiness can be severely damaged. The public may lose confidence in their ability to protect sensitive data, resulting in loss of customers, business partners, and competitive advantage.
Combating Unethical Hacking
Cybersecurity Measures

To combat unethical hacking, organizations and individuals must prioritize cybersecurity. Implementing robust security measures, such as firewalls, intrusion detection systems, encryption, and multi-factor authentication, can help prevent unauthorized access and mitigate the risks associated with cyberattacks.
Legal Actions

Governments around the world have enacted laws and regulations to deter and punish. Hackers caught engaging in illegal activities can face severe penalties, including fines and imprisonment. Legal frameworks aim to provide a deterrent effect and promote a safer digital environment.
Ethical Hacking as a Defense

Ethical hacking, conducted by certified professionals known as white hat hackers, plays a crucial role in defending against unethical hacking. By proactively identifying vulnerabilities and testing security systems, ethical hackers assist organizations in strengthening their defenses and preventing potential breaches.
Assumption
Unethical hacking poses a significant threat to individuals, organizations, and societies at large. The motivations behind unethical hacking range from personal gain to causing disruption or harm.The implications of these cyberattacks can be devastating, resulting in financial losses, privacy breaches, and damage to reputation. By implementing strong cybersecurity measures, enforcing legal consequences, and leveraging ethical hacking, we can take steps towards creating a safer digital landscape.
FAQs
FAQ 1: How can I protect myself from unethical hackers?
To protect yourself from unethical hackers, ensure you have strong and unique passwords, regularly update your software and devices, be cautious of suspicious emails or links, and use reputable antivirus software. Additionally, avoid sharing sensitive information on unsecured websites or public Wi-Fi networks.
FAQ 2: What are some famous cases of unethical hacking?
Famous cases of unethical hacking include the attacks on Equifax, Yahoo, and Sony Pictures. These incidents resulted in significant data breaches and financial losses.
FAQ 3: Are all hackers criminals?
No, not all hackers are criminals. There are ethical hackers, also known as white hat hackers, who use their skills to identify vulnerabilities and help improve cybersecurity.
FAQ 4: What is the role of ethical hacking in preventing unethical hacking?
Ethical hacking plays a vital role in preventing unethical hacking by identifying vulnerabilities in systems before malicious hackers exploit them. It helps organizations strengthen their security measures and protect against potential cyber threats.
FAQ 5: Is it possible to completely eliminate unethical hacking?
Although it may be challenging to entirely eradicate the issue, implementing proactive steps like strengthening cybersecurity, increasing awareness, and fostering ethical conduct can substantially diminish the risks associated with such endeavors.
